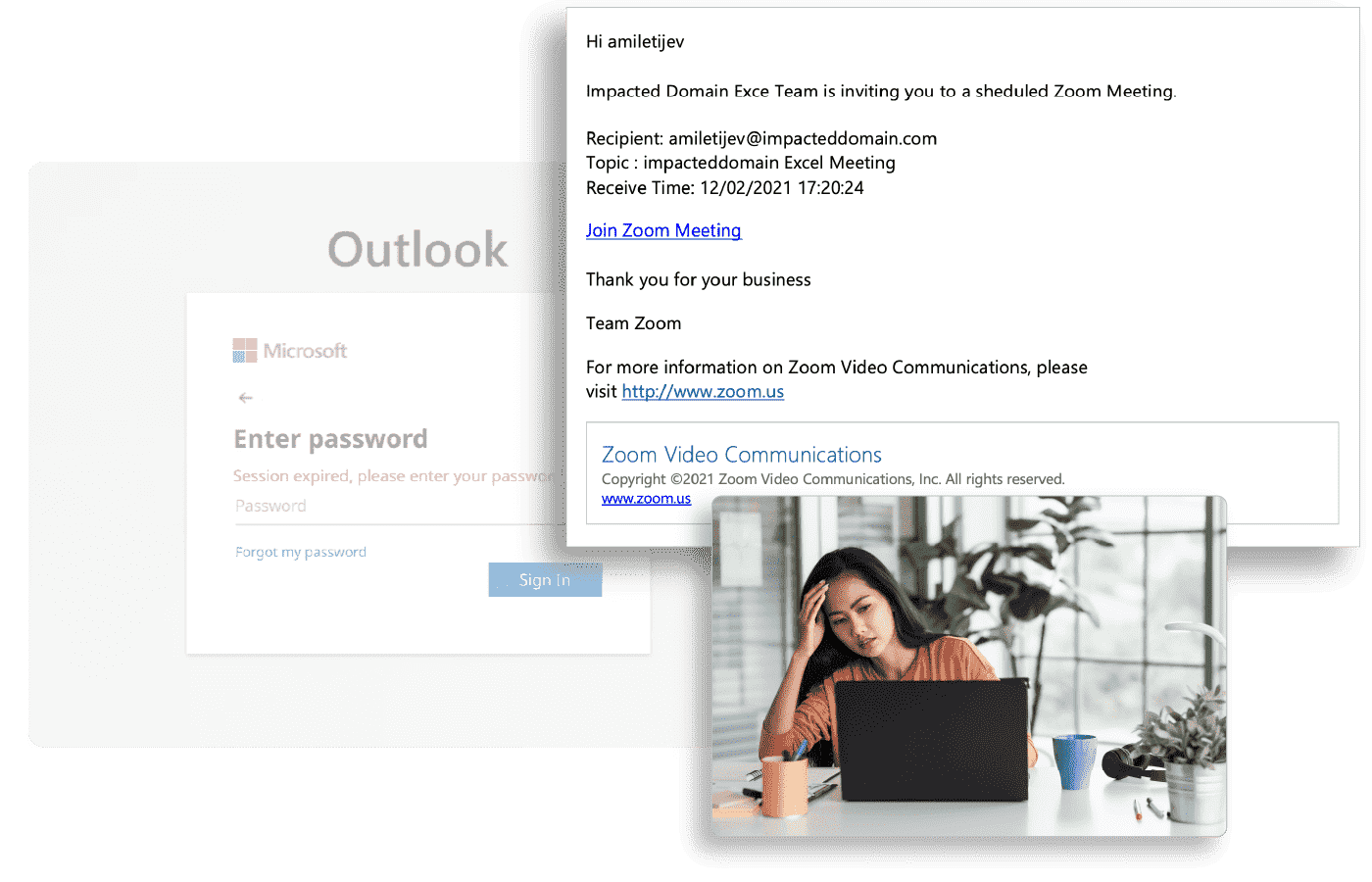
Supply Chain Impersonations
Organizations have a breadth of applications and vendors whom employees are used to receiving messages from, many with well-known logos and communication templates. In fact, business-related applications are the most frequently seen impersonation attempts across users at 45% of all attacks. Though these common brands, and templates allow for employees to more efficiently perform their duties, it also gives attackers an easy target to deliver Business Email Compromise (BEC) attacks. And, because the phish appears to be from a trusted brand or vendor applications, users are tricked into taking action sharing sensitive information.
Detecting Vendor Impersonations Attacks with GreatHorn
GreatHorn’s advanced anomaly detection uses artificial intelligence, machine learning and data science to automatically learn legitimate communication patterns between senders and recipients, identifying the anomalous emails, attachments, and links.
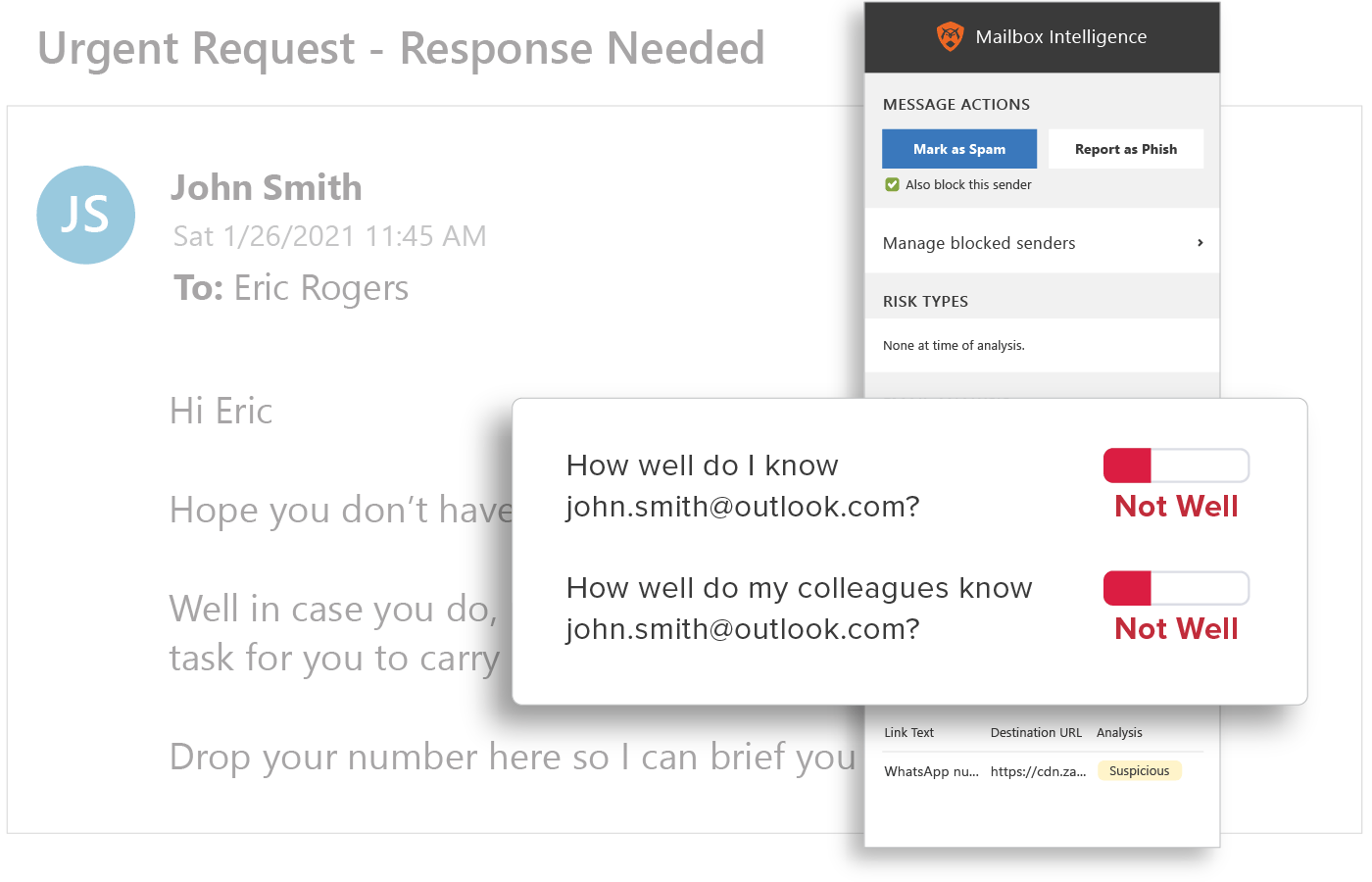
Behavioral Analytics
GreatHorn analyzes all communication patterns between senders and recipients using behavioral analytics within our AI and ML models, providing organizations with immediate detection and insight into anomalous emails.
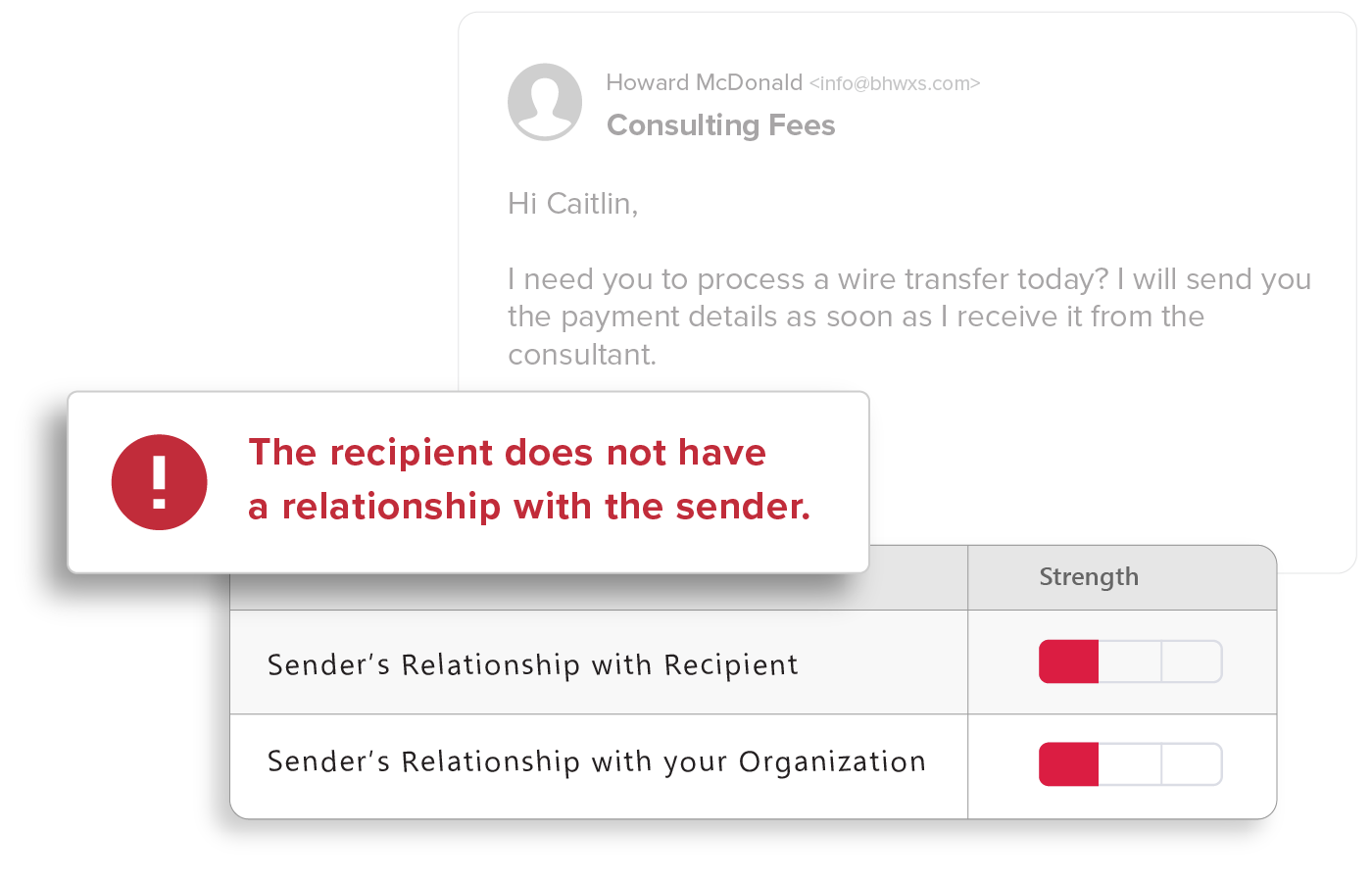
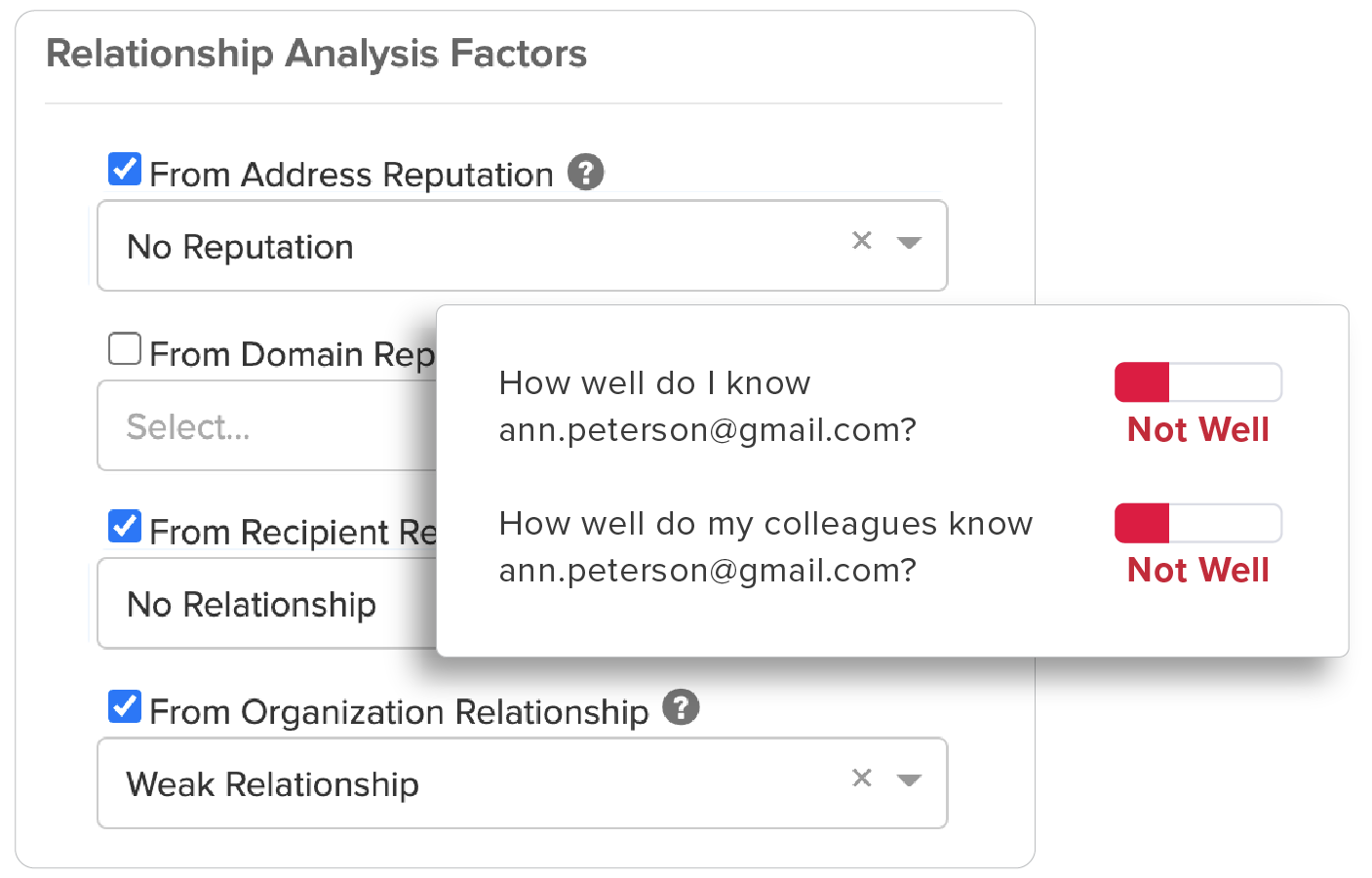
Relationship Strength
Strength of a sender’s individual relationship to the recipient, as well as a “friends of friends” system that accounts for the sender’s overall relationship with others in the recipient’s organization.
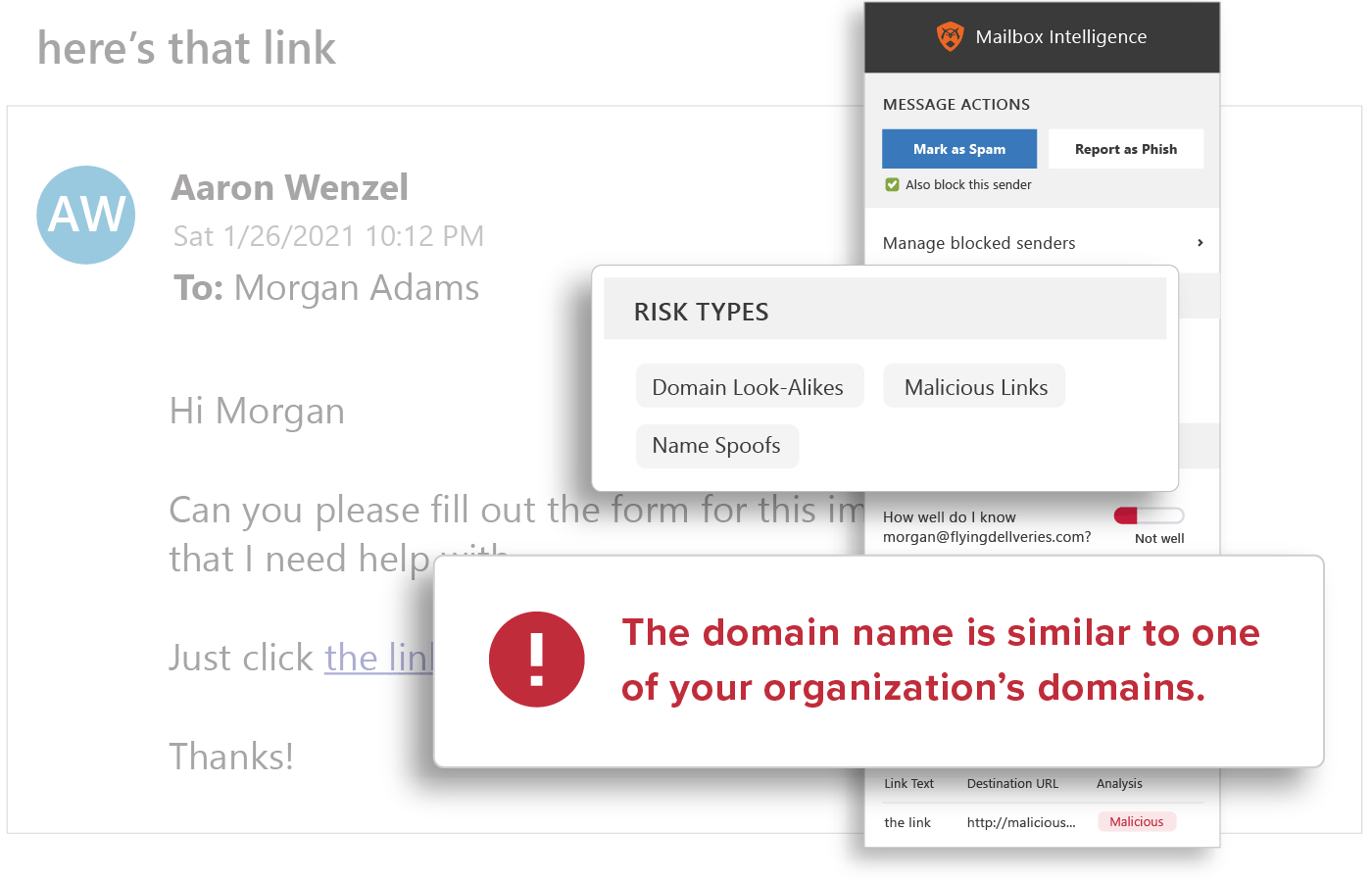
Spoofing Likelihood
Analysis for employee display name spoofs, domain spoofs, and domain look-alikes, including comparison against known email addresses, executive impersonation tactics, and email authentication standards.
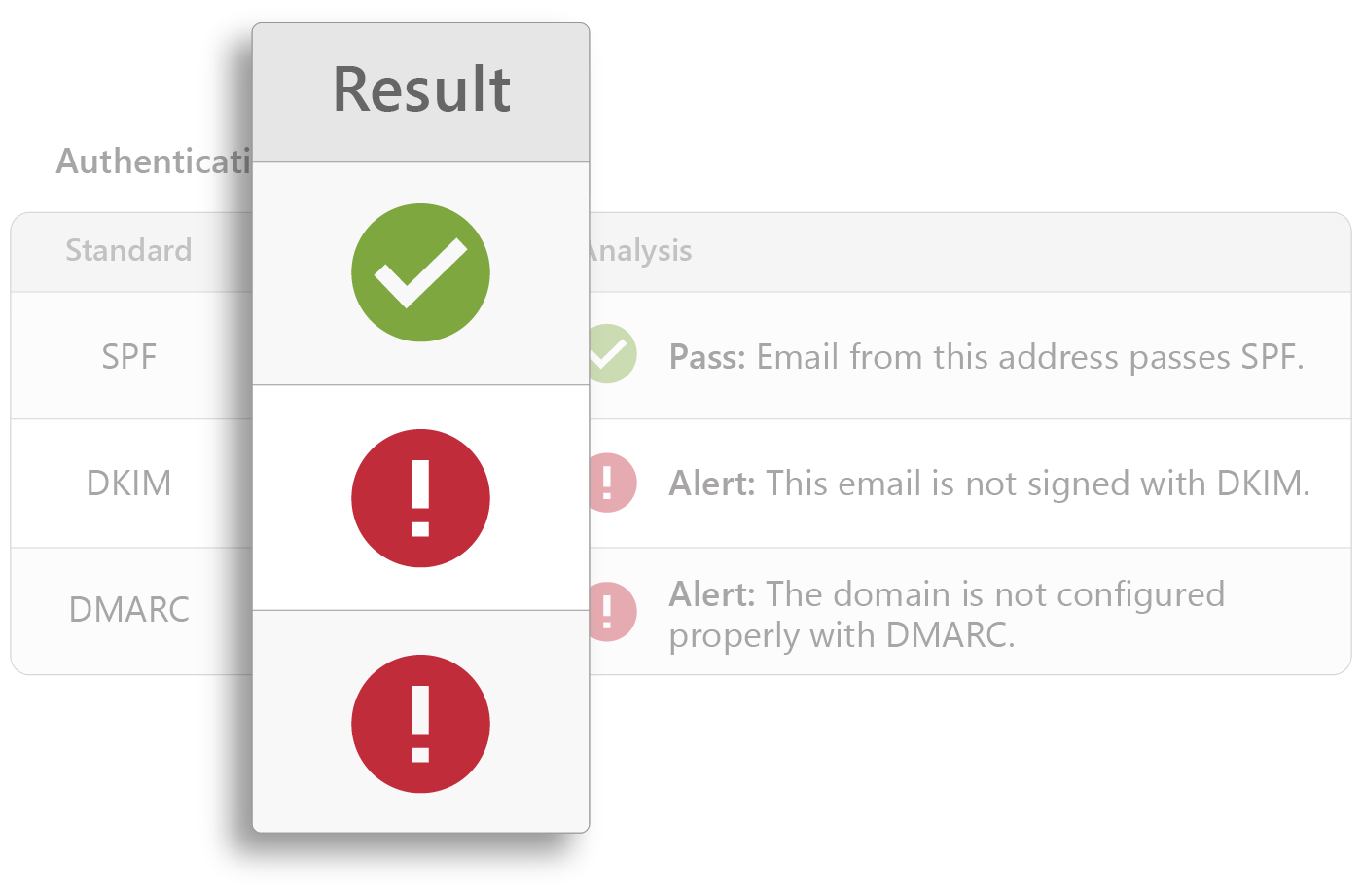
Technical Fingerprints
Sophisticated analysis of domain reputation, sending IP, and header information, including determining variations in expected authentication results for DMARC, DKIM, and SPF.
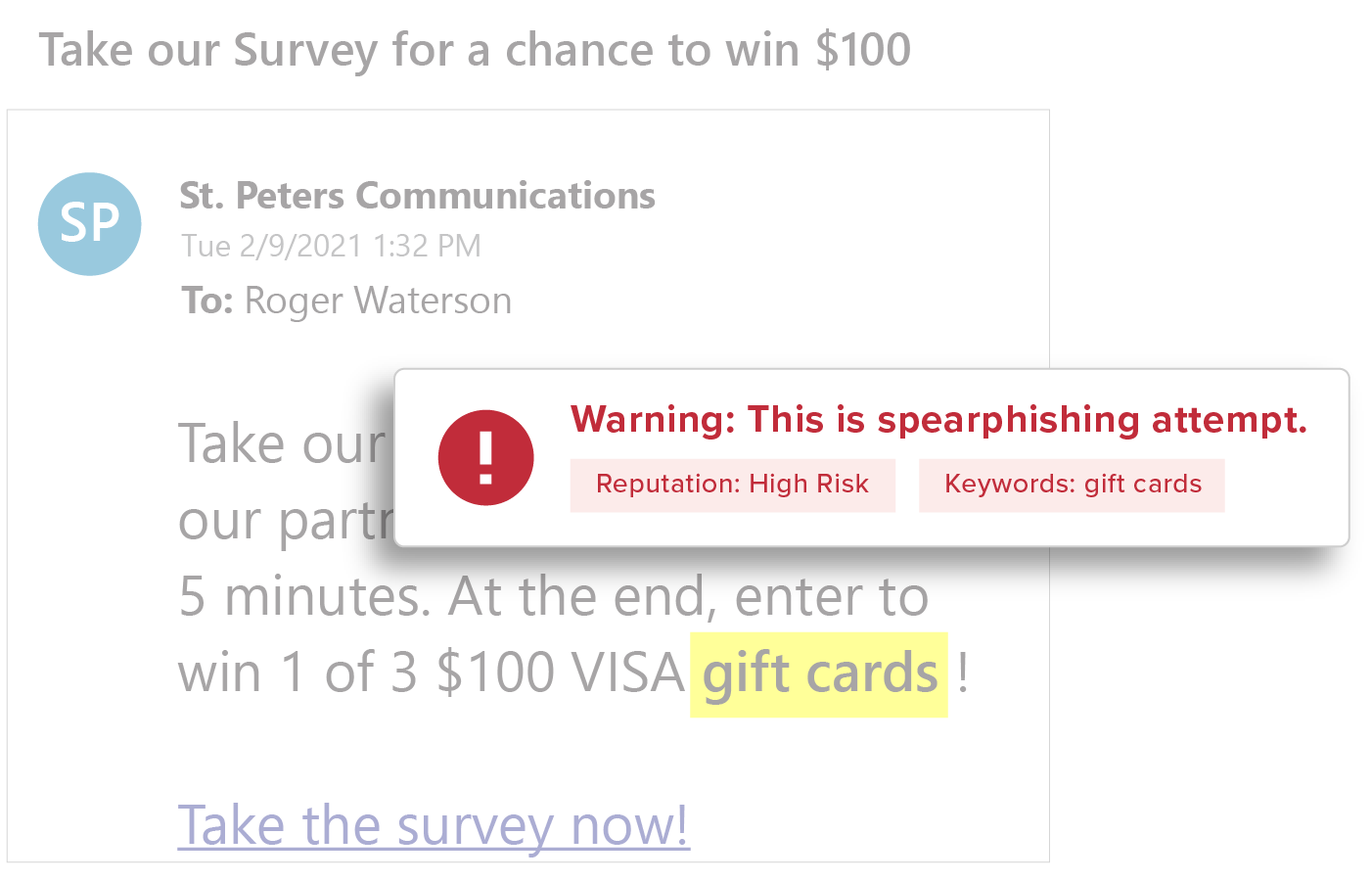
Content Analysis
Deep content inspection based on keywords, regular expressions (RegEx), attachments, and URLs, to identify common spear phishing tactics—wire transfer and W2 requests, credential theft attacks, business service impersonations—all without storing the content or the mail.
Communication Patterns
Establishes an understanding of communication patterns unique to a specific individual and a specific organization, such as email frequency, volume, recipients, sending patterns and more.
![[eBook] Things to Consider: Microsoft 365 + GreatHorn](https://www.greathorn.com/wp-content/uploads/2023/05/eBook-Microsoft-365-GreatHorn.png)
![[eBook] Things to Consider: Google Workspace + GreatHorn](https://www.greathorn.com/wp-content/uploads/2023/05/eBook-Google-WorkspaceGreatHorn.png)
![[Whitepaper] Measuring the Value of Email Security Solutions](https://www.greathorn.com/wp-content/uploads/2023/05/Whitepaper-Measuring-the-Value-of-Email-Security-Solutions.png)
![[Report] 2023 State of Email Security: Key Trends and Insights](https://www.greathorn.com/wp-content/uploads/2023/03/Report-2023-State-of-Email-Security.png)