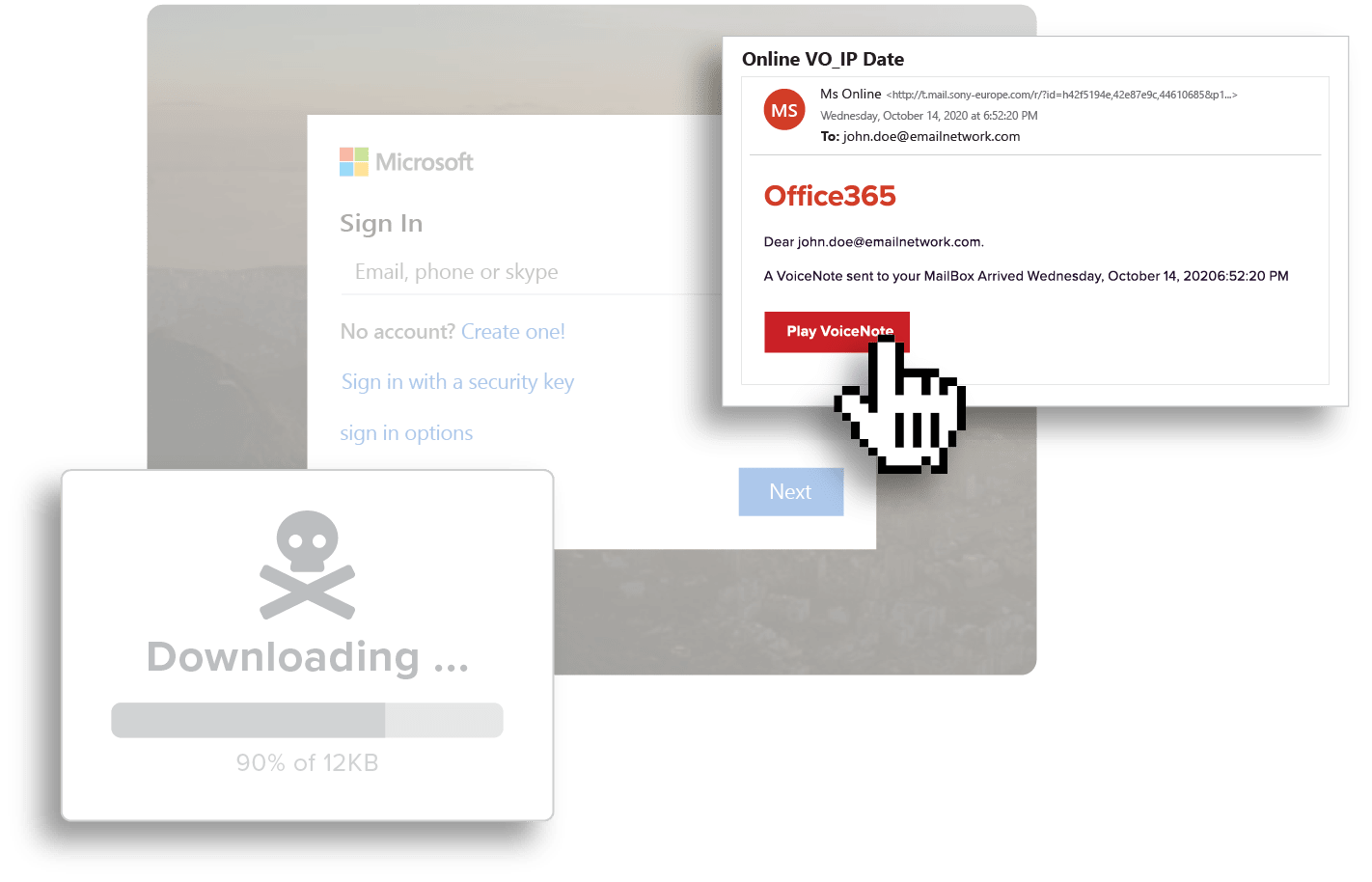
Detect Malicious Payloads
Cybercriminals are continually using social engineering techniques, including phishing campaigns, to access systems. Malicious payloads sent via phishing campaigns come in two common forms by cybercriminals – malicious attachments and URLs. Both are critical attack vectors that require mitigating controls.
Defending Against Malicious Payloads with GreatHorn
Applying a defense-in-depth strategy, GreatHorn detects attachment-based payloads and malicious websites through our AI, machine learning, and data science engines. GreatHorn also layers time-of-click analysis, so you’re protected against URLs that turn malicious, including zero-day attacks.
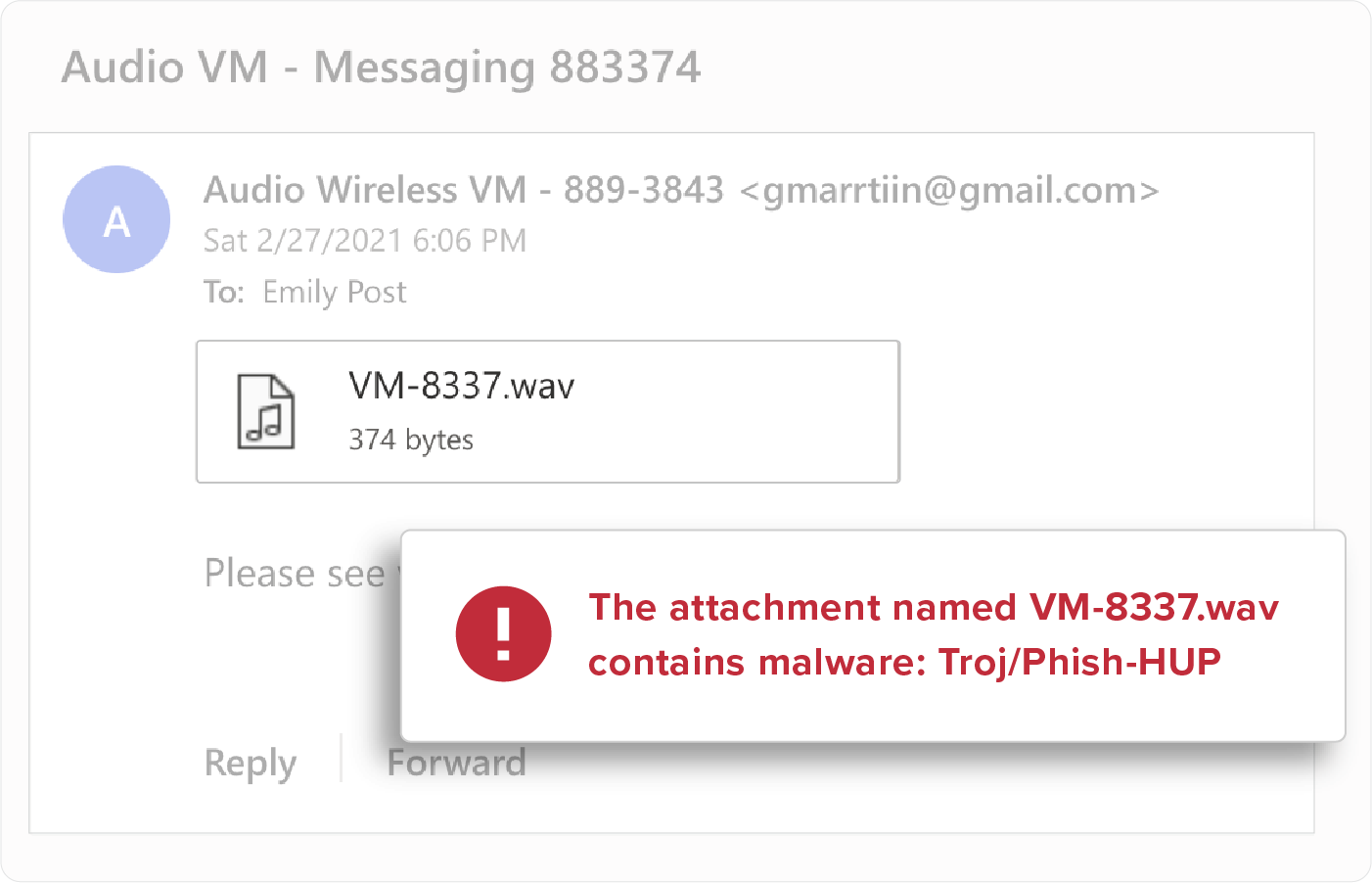
Attachment Inspection
Attachment types (ex: .SCR, .EXE, .PIF, .CPL, etc), file names, and content are scanned and inspected to detect malicious payloads. All malicious payloads are quarantined upon delivery to eliminate risk within the organization.
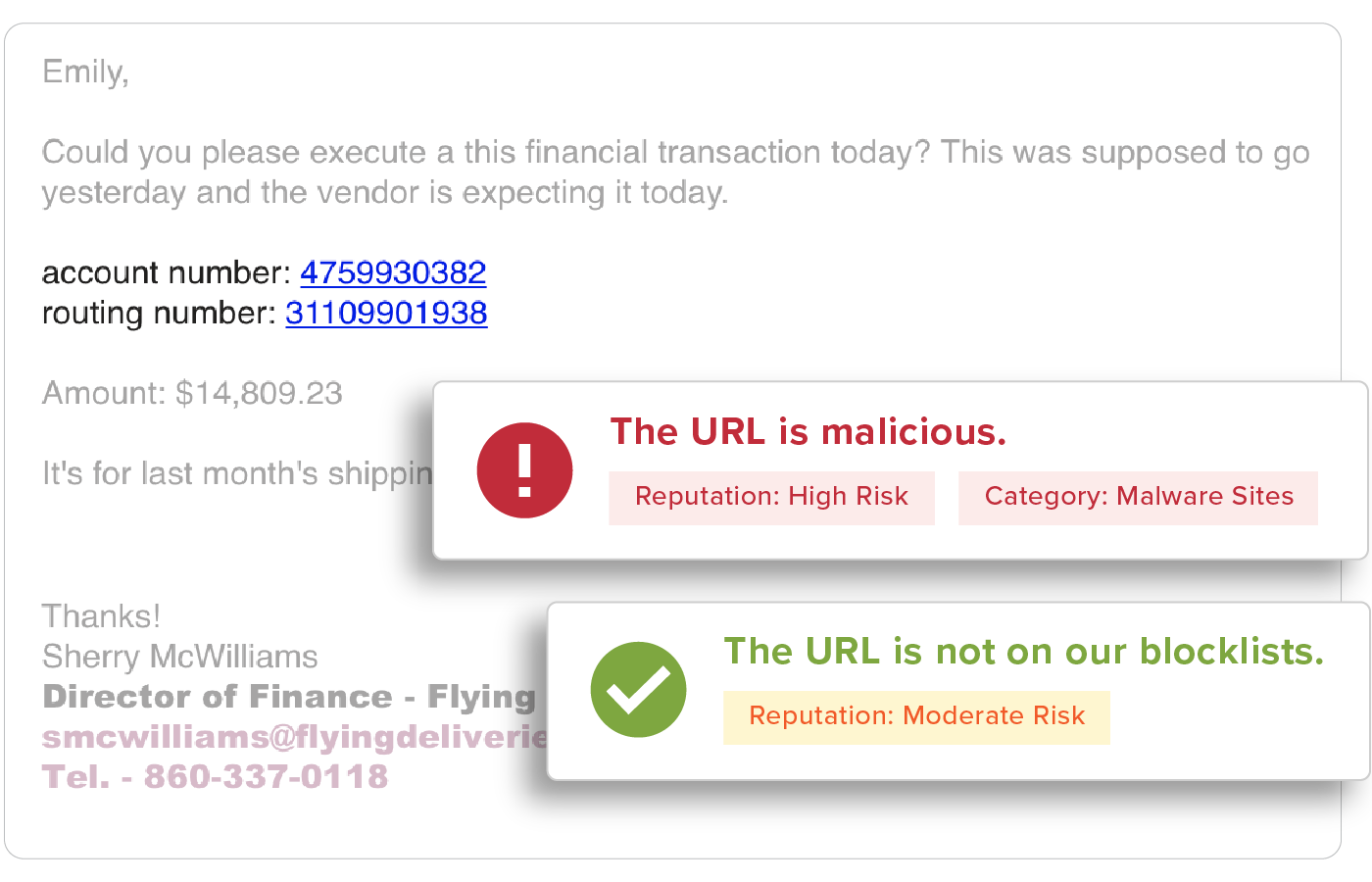
URL Inspection
URLs are easy to manipulate so that no two are delivered the same and are a top threat vector within phishing attacks. All URLs are inspected upon delivery to identify and detect malicious websites. GreatHorn also provides an additional layer of defense for suspicious URLs that turn malicious, using time-of-click analysis and computer vision to analyze suspicious links.
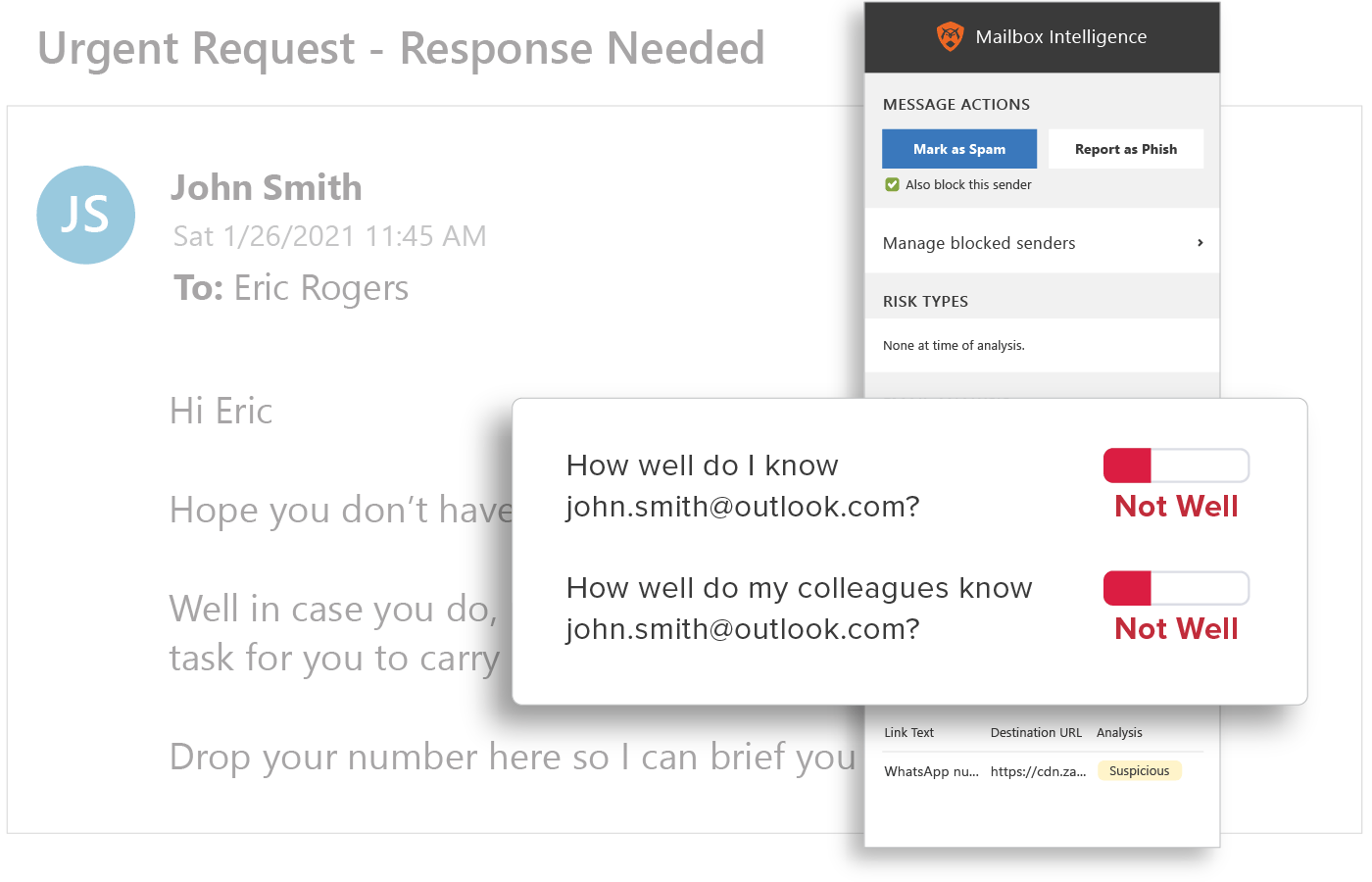
Behavioral Analytics
URLs are easy to manipulate so that no two are delivered the same and are a top threat vector within phishing attacks. All URLs are inspected upon delivery to identify and detect malicious websites. GreatHorn also provides an additional layer of defense for suspicious URLs that turn malicious, using time-of-click analysis and computer vision to analyze suspicious links.
![[eBook] Things to Consider: Microsoft 365 + GreatHorn](https://www.greathorn.com/wp-content/uploads/2023/05/eBook-Microsoft-365-GreatHorn.png)
![[eBook] Things to Consider: Google Workspace + GreatHorn](https://www.greathorn.com/wp-content/uploads/2023/05/eBook-Google-WorkspaceGreatHorn.png)
![[Whitepaper] Measuring the Value of Email Security Solutions](https://www.greathorn.com/wp-content/uploads/2023/05/Whitepaper-Measuring-the-Value-of-Email-Security-Solutions.png)
![[Report] 2023 State of Email Security: Key Trends and Insights](https://www.greathorn.com/wp-content/uploads/2023/03/Report-2023-State-of-Email-Security.png)