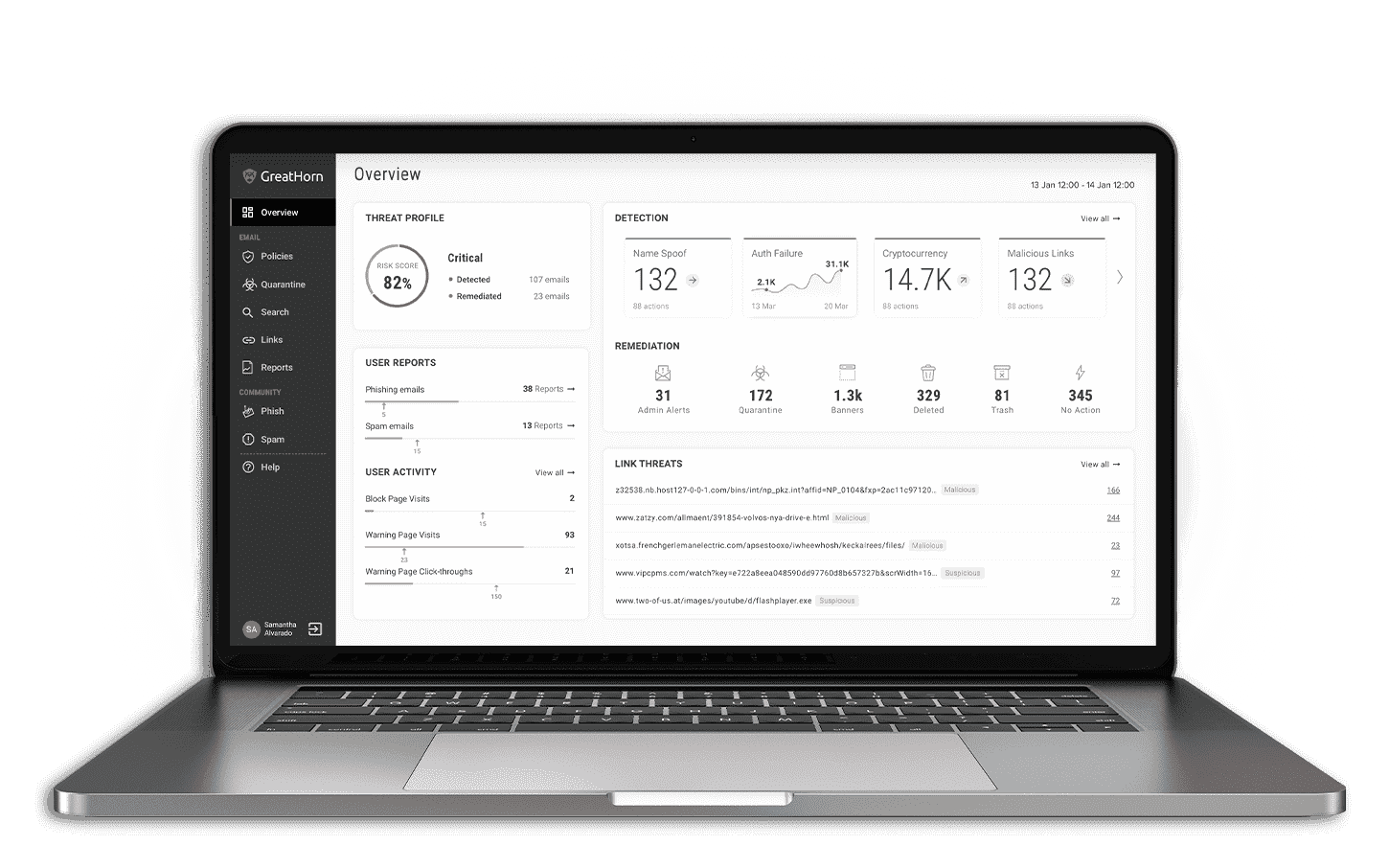
Reduce the Risk of Account Takeover
Protect Against Internal Threats
The risk of account takeover has increased exponentially. Yet identifying compromised email accounts can be tricky – often showing up only after there’s been financial and reputation damage. Implementing multi-factor authentication won’t protect users from cell-jacking, unattended and unlocked devices, or phone-based social engineering.
GreatHorn Account Takeover Protection provides a low-friction, secondary layer of authentication that’s easy to implement, difficult to bypass, and minimally disruptive for employees.
Account Takeover Protection
Use biometric authentication to verify employee identities, reducing exposure from any compromised accounts.
Credential Theft Detection
Prevent employees from accessing password-stealing accounts by using computer vision to analyze suspicious links.
Internal Email Protection
Analyze internal email the same way as external – taking into account relationships, communication patterns and more.
Get Your FREE Email Threat Assessment
Learn what advanced threats are currently getting through your existing email security and into your end users’ mailboxes.
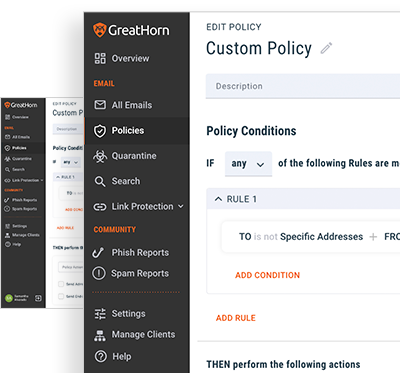
The Only Defense Against Account Takeover Attacks
Most solutions claiming to provide account takeover protection use behavioral cues to try to identify account takeover – but can’t actually verify the sender’s identity.
GreatHorn actually validates the identity of a sender using biometric authentication.
Simple Easy Identification – No Devices Required
Your typing pattern is automatic, always available, and unique to you. Account Takeover Protection uses machine learning techniques to capture an employee’s unique typing pattern on both desktop and mobile devices – analyzing the dynamics of an employee’s keystrokes, such as speed, pressure, and timing between key press and release. We don’t capture the keystrokes themselves.
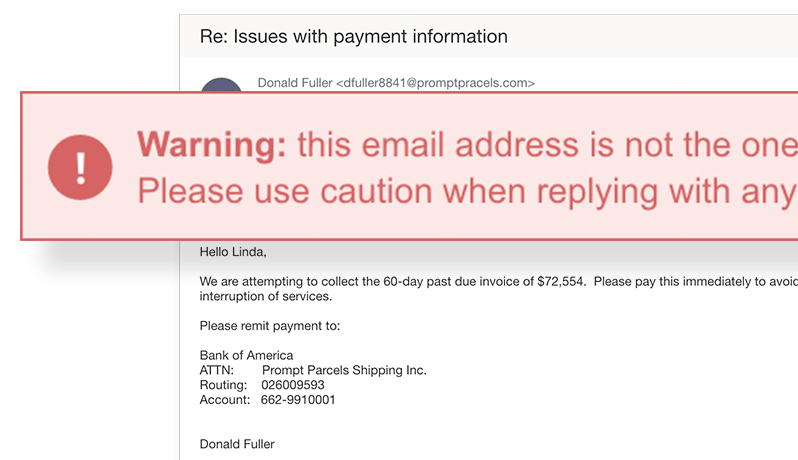

Ongoing maintenance and support
When your business is compromised by a phishing attack, every second counts. With GreatHorn’s proactive managed email security offering, you receive GreatHorn’s technical expertise, combined with our best-in-class cloud email security solutions, optimized to the level you need to maintain the most advanced email security posture.
Key Benefits
Difficult to Bypass
Authentication is trustworthy and difficult to replicate as it’s based on biometric data
Minimally Disruptive
Initial setup and ongoing verification is as simple as typing an email address
Simple Implementation
Administrator roll-out via Outlook plugin – no additional apps to download
Configurable Actions
Failure actions can be adjusted based on risk tolerance or group – from a simple alert to send prevention
Mobile-friendly
Supports mobile, desktop, and web interfaces to ensure protection regardless of access method
Compatible with Other Solutions
Use in conjunction with multi-factor authentication or identity access management solutions
![[eBook] Things to Consider: Microsoft 365 + GreatHorn](https://www.greathorn.com/wp-content/uploads/2023/05/eBook-Microsoft-365-GreatHorn.png)
![[eBook] Things to Consider: Google Workspace + GreatHorn](https://www.greathorn.com/wp-content/uploads/2023/05/eBook-Google-WorkspaceGreatHorn.png)
![[Whitepaper] Measuring the Value of Email Security Solutions](https://www.greathorn.com/wp-content/uploads/2023/05/Whitepaper-Measuring-the-Value-of-Email-Security-Solutions.png)
![[Report] 2023 State of Email Security: Key Trends and Insights](https://www.greathorn.com/wp-content/uploads/2023/03/Report-2023-State-of-Email-Security.png)