The shift from on-premise email platforms to cloud email platforms has taken shape, with the...
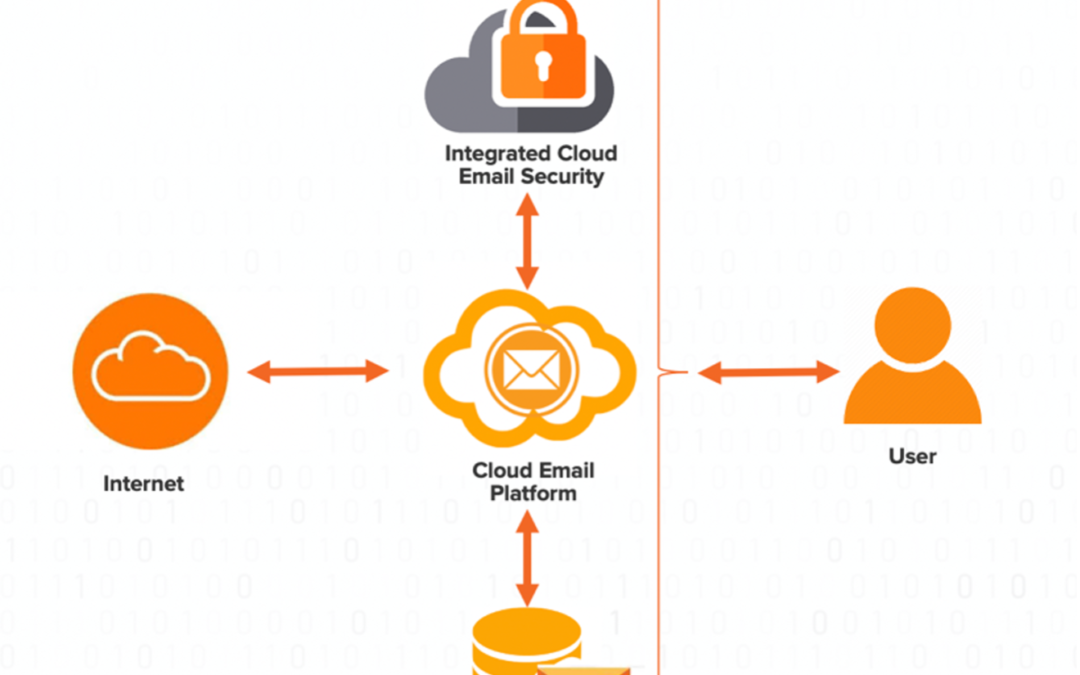

The shift from on-premise email platforms to cloud email platforms has taken shape, with the...
This article relates to an on-going phishing campaign, and the GreatHorn Threat Intelligence team...
Any organization involved in U.S. politics and elections - either directly or indirectly - is a...
Phishing attacks are one of the most common security challenges that organizations and individuals...
In the not too distant past, traditional work offices and co-working spaces were the norm, along...
In today’s world, disinformation is common, skewing reality from fiction. It’s a place where...
Missed our webinar? Don’t worry – we’ve still got you covered. On September 17, 2020, Holger...