How to Protect Against Microsoft Subdomain Takeover
In a blog post today, Vulnerability released research highlighting the risk of hundreds of Microsoft subdomains that are vulnerable to takeover. First reported by Zak Doffman in Forbes, the vulnerability is both potentially widespread and insidious – creating the opportunity for criminals to exploit loopholes in both security tools and end user training to gain access to credentials, confidential information, or to distribute malware.
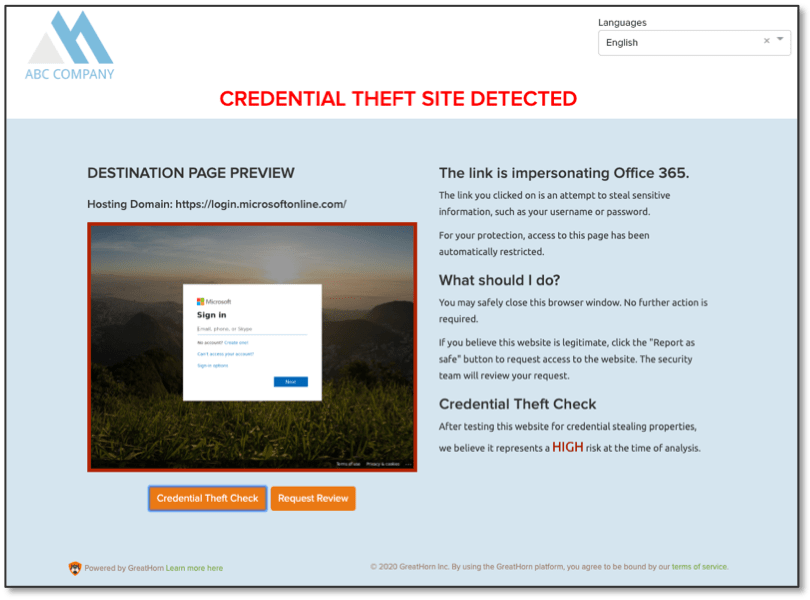
According to Forbes, hackers can easily identify exposed Microsoft subdomains, then “hijack them, stealing cookies and credentials and bypassing open redirection protection” as most Microsoft subdomains appear to be whitelisted. The result is that the hacker then has full control of that subdomain and can, for example, clone the main office.com login page for credential theft.
This technique bypasses even the most elite anti-spam and email security tools, most of which conduct checks at the domain level rather than the subdomain level. Meanwhile even the most diligent user is vulnerable – typical end-user training recommends checking email link for the expected domain – an email asking for identity verification with a URL beginning identityhelp.microsoft.com would easily be assumed to be safe by the user.
The security industry has long attributed breaches and successful phishing attacks to poorly educated or careless users, but as this technique reinforces, criminals can – with relatively little effort – create highly sophisticated and believable phishing campaigns that can fool even the most savvy of users.
Such sophisticated attacks require a multi-pronged approach to protection.
First, the detection of potential threats – GreatHorn’s robust threat analysis engine analyzes hundreds of different factors – deep URL analysis, relationship analytics, and communication patterns among them, to determine the relative risk of an email. This analysis engine is exposed to both GreatHorn’s threat intelligence team as well as to customers, enabling either to quickly build a custom policy based on emerging threat patterns such as this one.
Second, credential theft analysis based on computer vision. As part of its link protection capabilities, GreatHorn runs a time-of-click analysis on all suspicious links to determine if the site appears to be a common login page (e.g. Microsoft Office) and compares that data with our URL analysis to determine if it is a credential theft site.
Third, GreatHorn’s robust search capabilities enable security teams to quickly identify, investigate, and remove any outstanding links in the environment that meet unique search criteria (e.g. Microsoft links that include a subdomain).
As a final barrier, GreatHorn Account Takeover Protection (announced last week) protects organizations from stolen credentials. By using an individual’s unique typing patterns as a means of biometric authentication, Account Takeover Protection can identify email accounts that have been compromised, flagging them for review, and optionally warn recipients or prevent email from being sent.
In the meantime, for non-GreatHorn customers, our recommendation based on this current attack is for users to be cautious of all emails linking to Microsoft related sites that include a subdomain, and when in doubt, to login to Microsoft products directly rather than through a link in an email.
While Microsoft is the focus here (and certainly the rise in Office 365 adoption has made Microsoft credential theft attacks commonplace), it’s critical to note that Microsoft isn’t the only domain subject to this vulnerability – many other common domains are as well, so the advice and strategy outlined here applies equally to non-Microsoft domains.


