Does Manual Search and Remediation of BEC Phishing Attacks Take You Hours?
Don’t burn your hours using cumbersome Powershell scripting, or spend time manually located phish to remove similar copies across your organization. Instead, use a solution that can automate incident response and remediate phishing attacks.
 Learn how you can improve your response to sophisticated threats, with:
Learn how you can improve your response to sophisticated threats, with:
- Granular search functionality across the entire email envelope to identify all emails with matching criteria
- Immediate identification and quarantine of individual or bulk emails across your entire email environment
- Preconfigured integrations and open APIs allows you to build workflows across your security solutions
- Leveraging fact-based AI engine to assess risk
Download the Whitepaper
"GreatHorn perfectly combines power and flexibility with the simplicity of an API solution."
— Director Of IT in the Services Industry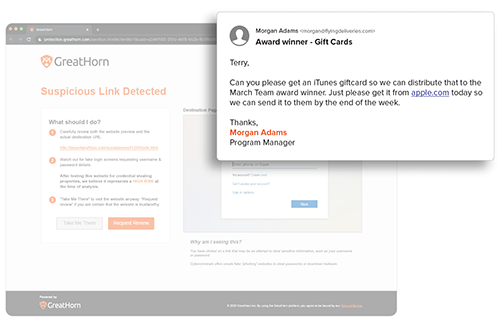
Suspicious URL Detection
URLs are analyzed using machine vision to detect any anomalous content on the destination. With GreatHorn’s Link Protection page, users are educated with a preview of the destination, the risk of credential harvesting, and steps they should take to minimize their risk.
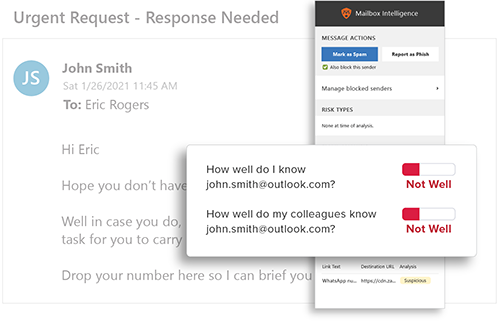
Behavioral Analytics
GreatHorn analyzes all communication patterns between senders and recipients using behavioral analytics within our AI and ML models, providing organizations with immediate detection and insight into anomalous emails.
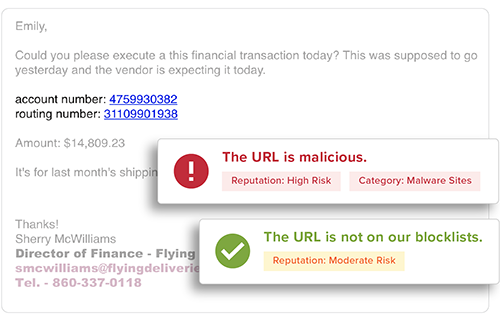
End User Education
Provide users with the context they need to help them make better decisions by applying automated and customized banners, Mailbox Intelligence, Suspicious Link pages, and more.