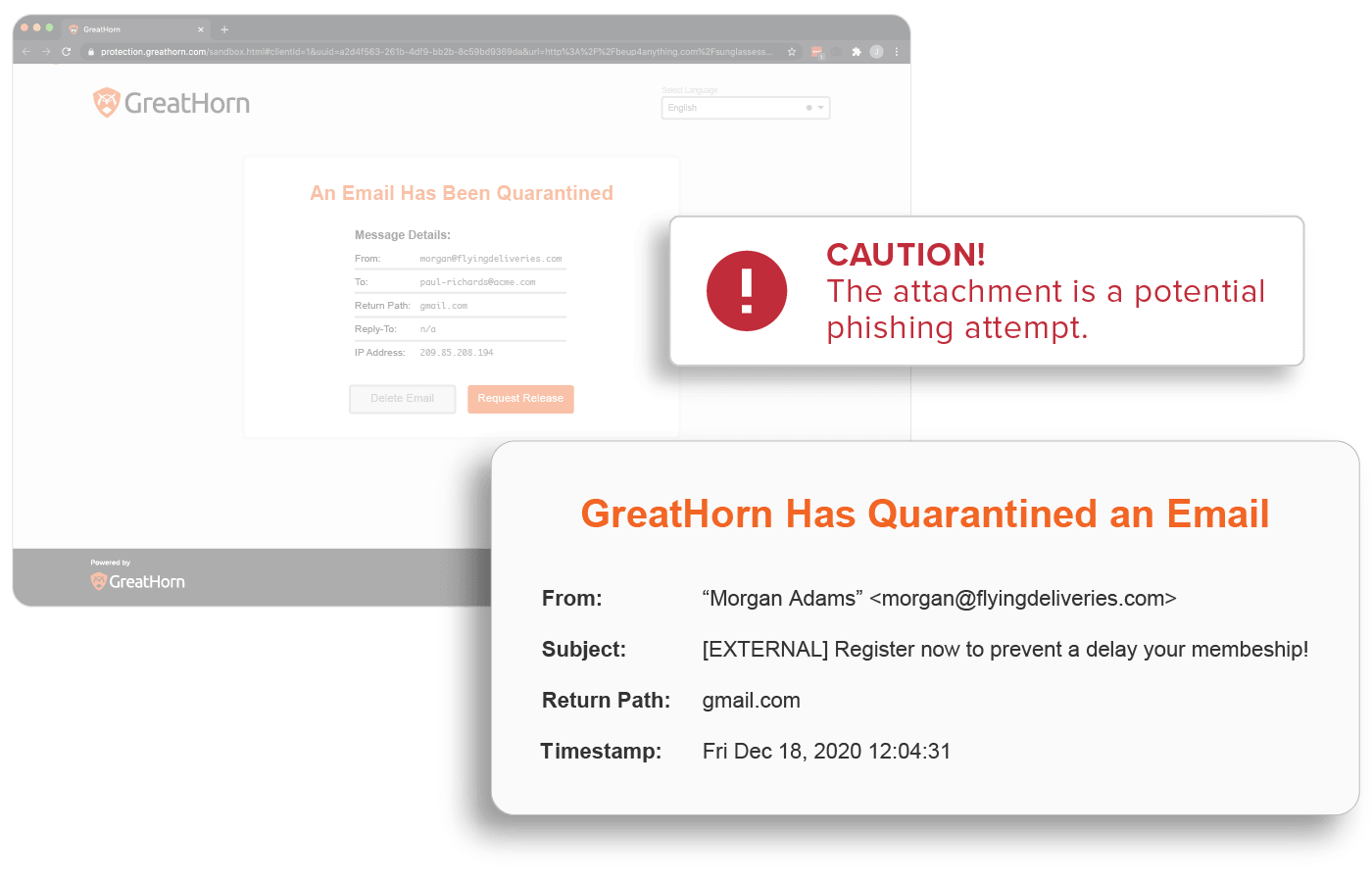
Payment Fraud Protection
Payment fraud can leverage multiple techniques to successfully execute the phishing attack. GreatHorn is the only vendor who offers a layered approach to detect all areas of risk represented in an organization and provide automated controls to mitigate risk across all attack vectors.
Detecting Payment Fraud Attacks with GreatHorn
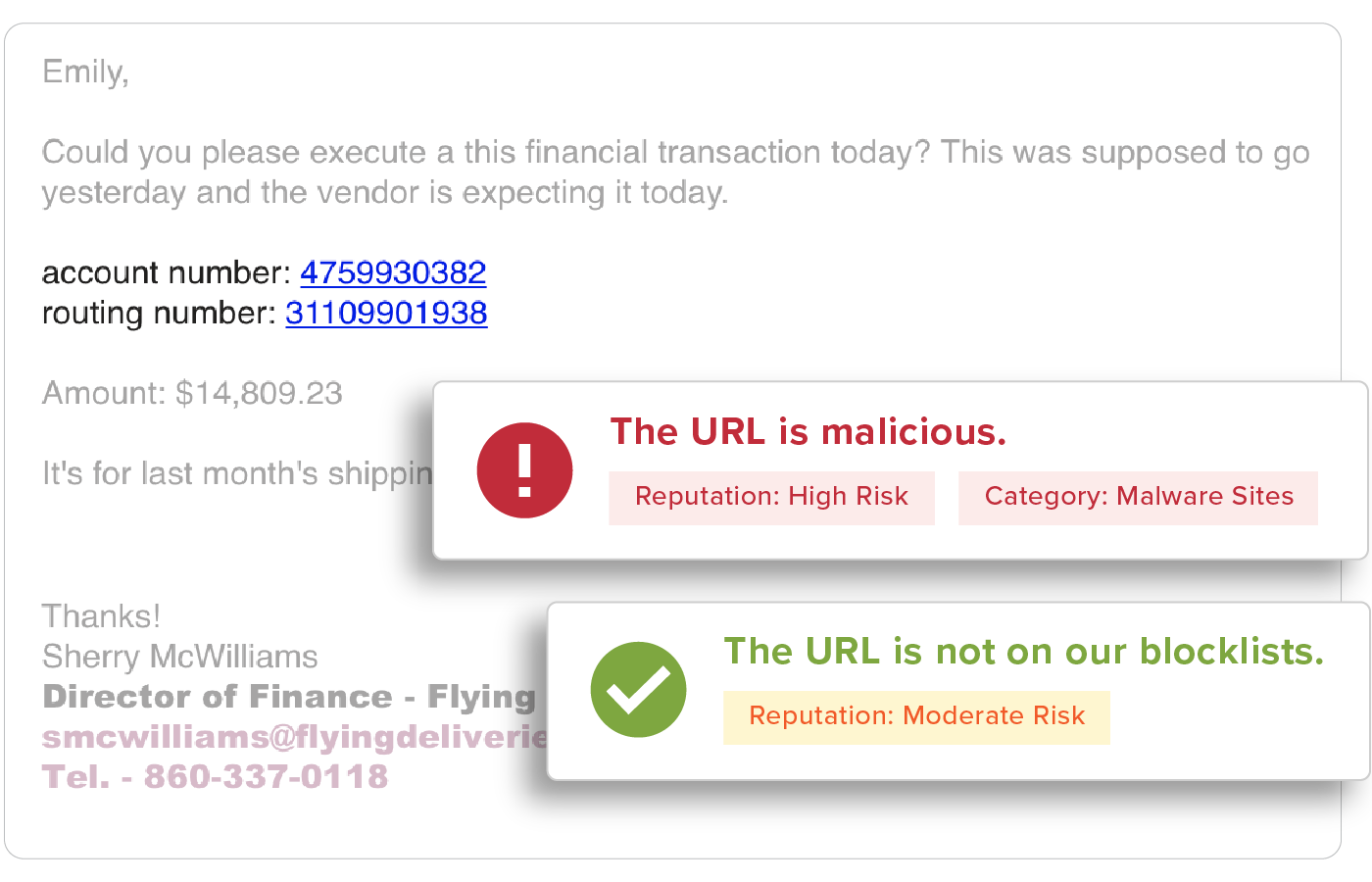
Attackers often use phish to deliver fraudulent invoices and payment methods, troubling many organizations. In fact, phishing attacks using payment fraud have resulted in some of the largest financial losses to-date. Whether it’s an attacker who has gained access to a legitimate user’s account to perform internal spearphishing or an impersonation attack, they use fraudulent invoices and routing numbers to trick users into completing the payment.
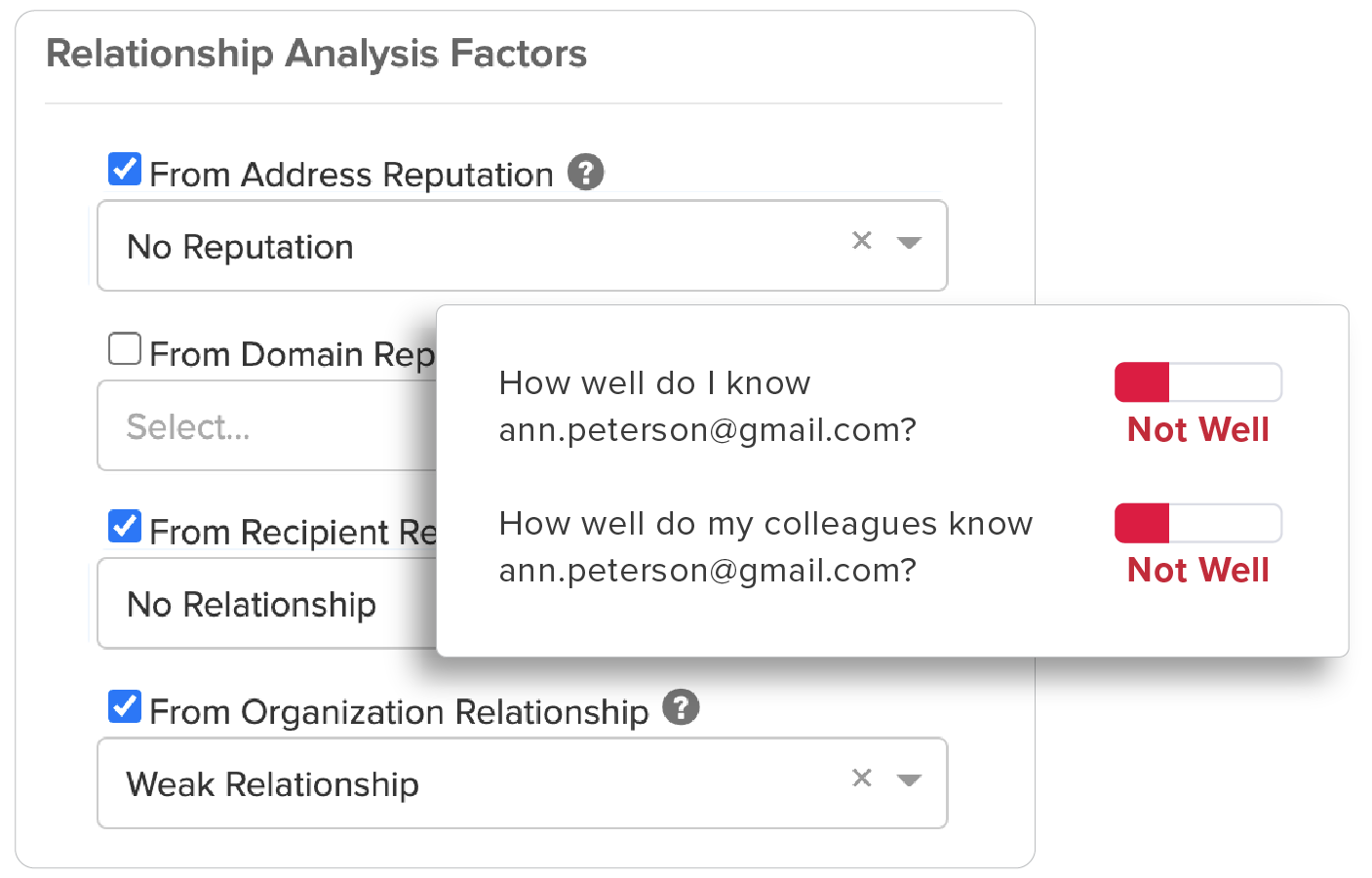
Relationship Analytics
GreatHorn analyzes all communication patterns between senders and recipients using behavioral analytics within our AI and ML models, providing organizations with immediate detection and insight to take action.
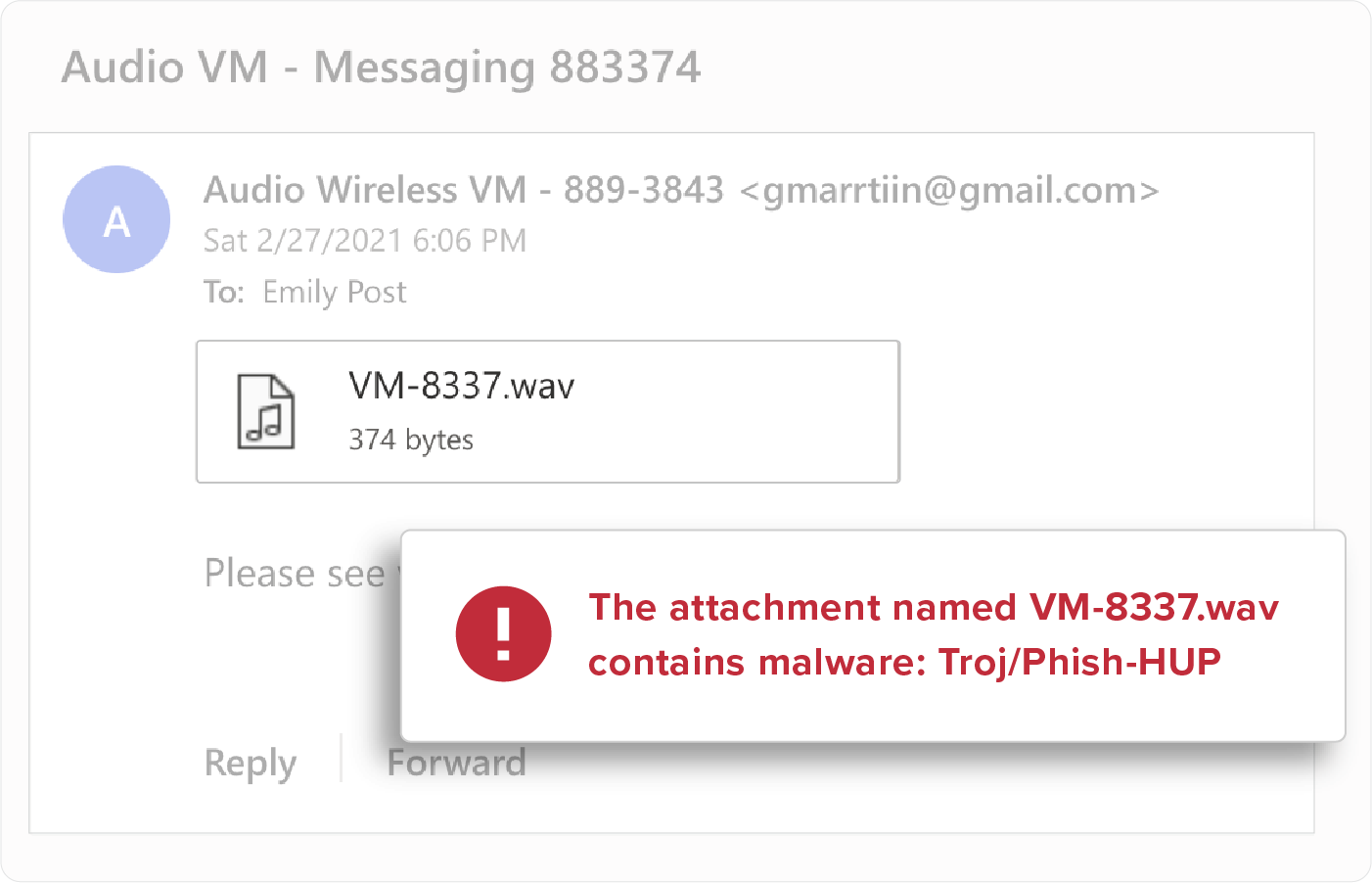
Attachment Inspection
Attachment types (ex: .SCR, .EXE, .PIF, .CPL, etc), file names, and content are scanned and inspected to detect malicious payloads. All malicious payloads are quarantined upon delivery to eliminate risk within the organization.
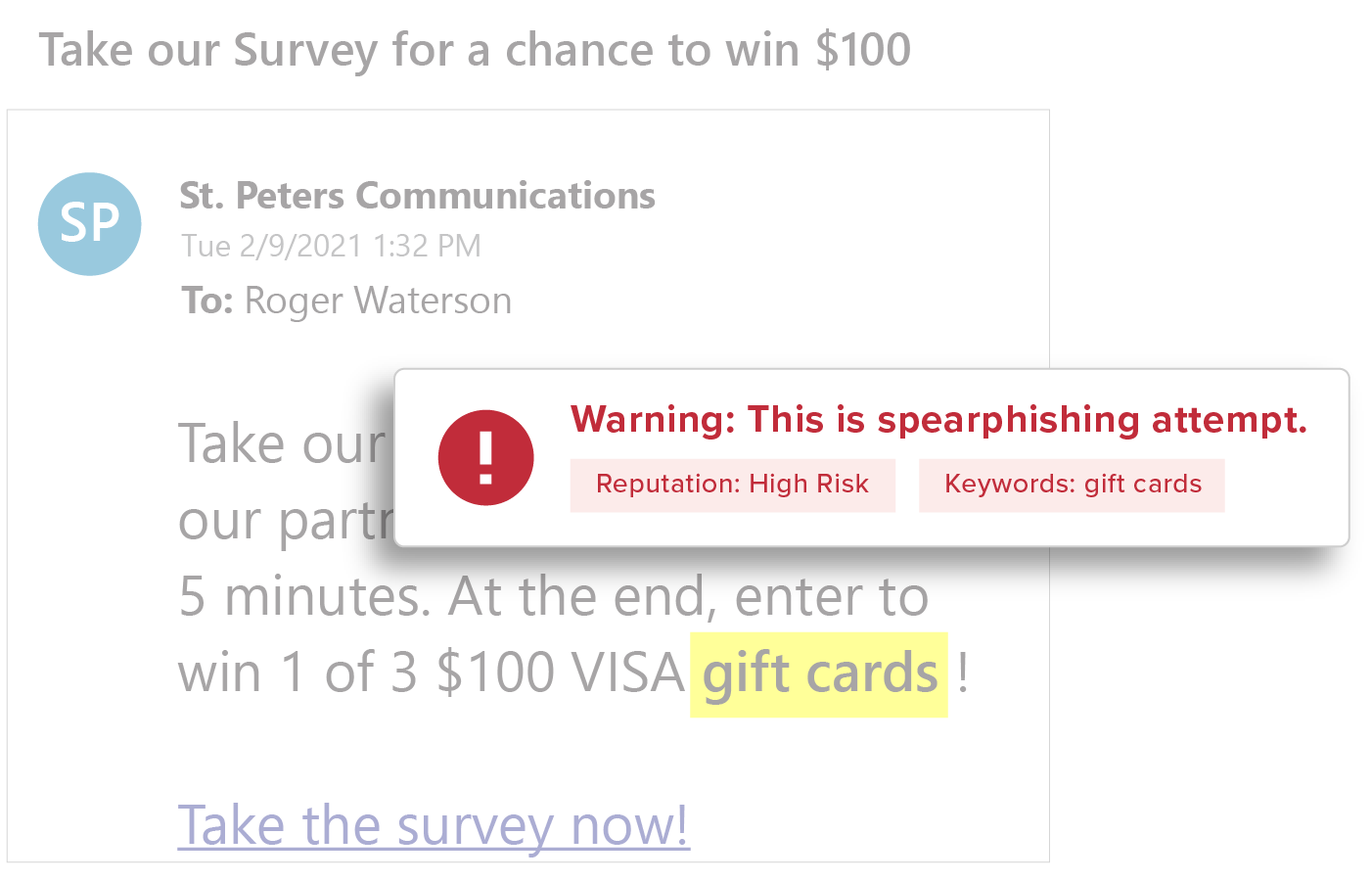
Content Inspection
By analyzing all message copy, keying off keywords, and patterns within GreatHorn’s AI and machine learning models, automated risk types can apply a wide range of controls based on the recipient’s risk profile within your organization.
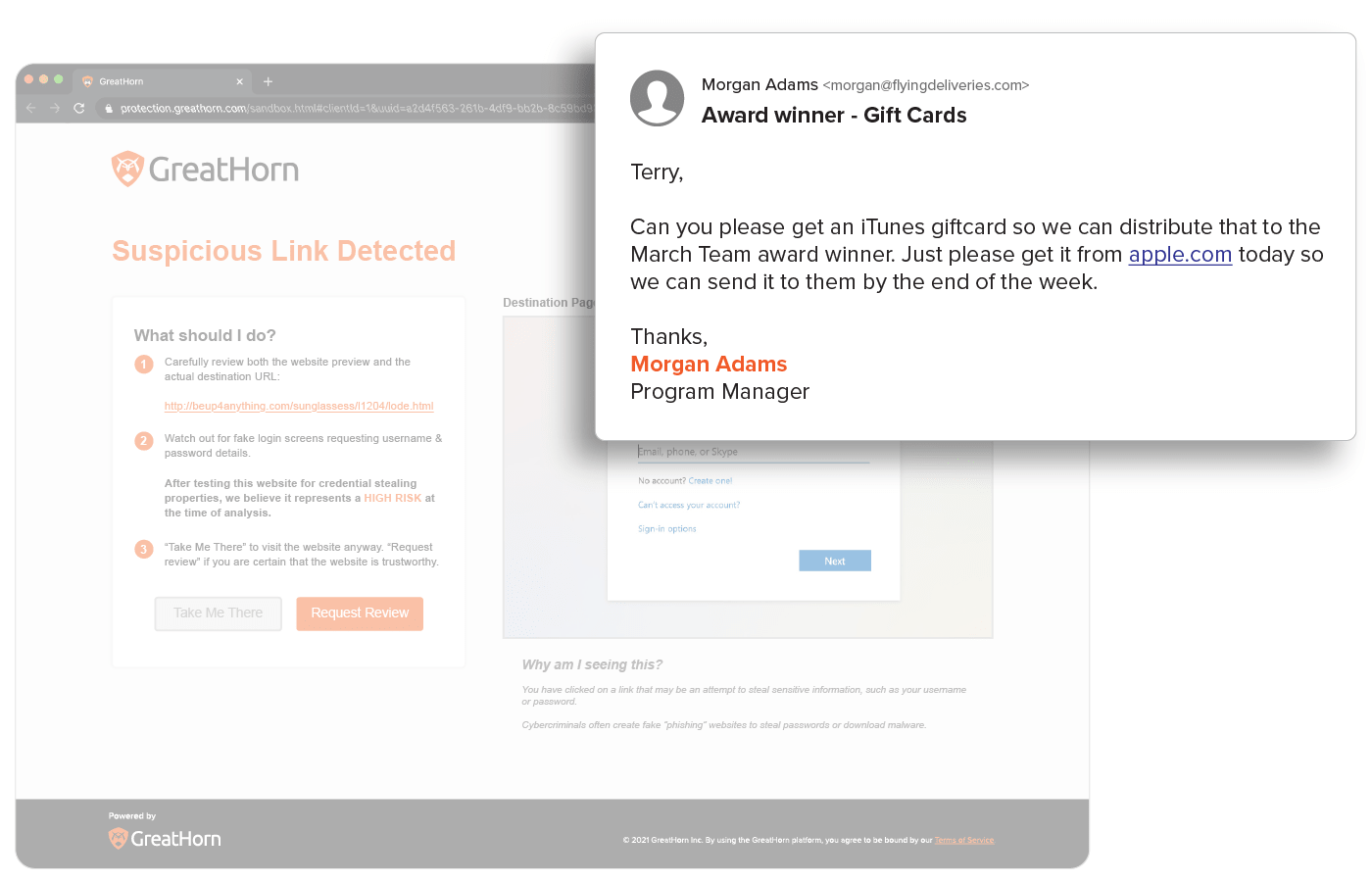
Suspicious and Malicious URL Detection
URLs are easy to manipulate so that no two are delivered the same and are a top threat vector within phishing attacks. All URLs are inspected upon delivery to identify and detect malicious websites. GreatHorn also provides an additional layer for suspicious URLs that turn malicious, using time-of-click analysis using computer vision to analyze suspicious links.
End User Education
Provide users with the context they need to help them make better decisions by applying automated and customized smart banners, Mailbox Intelligence, Suspicious Link pages, and more.
![[eBook] Things to Consider: Microsoft 365 + GreatHorn](https://www.greathorn.com/wp-content/uploads/2023/05/eBook-Microsoft-365-GreatHorn.png)
![[eBook] Things to Consider: Google Workspace + GreatHorn](https://www.greathorn.com/wp-content/uploads/2023/05/eBook-Google-WorkspaceGreatHorn.png)
![[Whitepaper] Measuring the Value of Email Security Solutions](https://www.greathorn.com/wp-content/uploads/2023/05/Whitepaper-Measuring-the-Value-of-Email-Security-Solutions.png)
![[Report] 2023 State of Email Security: Key Trends and Insights](https://www.greathorn.com/wp-content/uploads/2023/03/Report-2023-State-of-Email-Security.png)